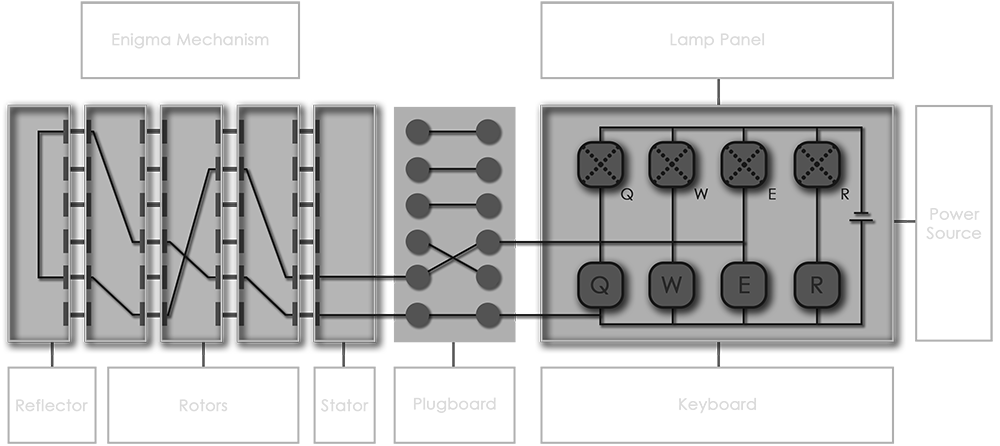
Components
The machine features components that remained throughout its production. Out of all the components only the rotors are removable, in some occasions the reflector is removable as well.
A number of rotors are interchangeable between some machines. Although each variant has exact specifications that are noticeable to a trained eye, there are many examples of the same
machines with different manufacturing characteristics. This was due to different companies manufacturing similar machines. In some cases, that was also due to the time period they were
manufactured in. Initially the machine mostly incorporated die-cast components and was very robust. As the war raged on, Germany started having a limited recourse of raw materials. There
are a number of variants found depicting this, on these machines many components are constructed from Bakelite, an early plastic. This is reflected to all extends where same variants have
been found with components constructed out of a different material.
Stator
The stator is a type of static wheel which was originally named the Entrittswalze (ETW). It is the entry and exit point of the signal passing through the rotors and the reflector. It
does not move and is placed on the rightmost side of the mechanism, before the first rotor placed on the right position.
The only purpose of the stator is simply to transfer the signal into the rotors from the wires connected to the keys and mechanism. It has twenty-six contacts on its left side. Most
Enigma's have the same ordered stator. It is ordered in the same way as the keyboard from Q to Z. Some models like the M4 have the stator arranged in an alphabetical order. The Tirpitz
Enigma is the only model which has the stator ordered in a randomised fashion.
Rotor
The rotors are the most significant part of the Enigma. They are the actual components that carry out most of the cryptographic procedure. Its actual name was Walze which can be
defined as Wheel or Rotor. Most machines where supplied with three rotors. Some machines have a variety which ranges up to eight rotors. In cases the rotors would be rewired to increase
security.
Each rotor has some distinctive characteristics. It has twenty-six positions from A to Z. On either side there are also 26 contacts aligned in a circular fashion. They are
interconnected to the other side in a specific randomised fashion. The index of the rotor is engraved along the side. It is either marked as A to Z or 01 to 26. In addition, each rotor
has a ring that can be used to offset the wiring arrangement. It is regarded as creating an offset in the opposite direction. A final component is the notches which are fixed on the side
of the rotor and cannot be altered.
Most rotors present exactly the same characteristics. The obvious differences are the offset ring construction and index labelling. They had the same size and notch construction to
accommodate ratchets and pullers. In Type G machines the notch construction is altered to endorse the cog-wheel mechanism. The Enigma G-312 had a smaller body which implies that the
rotors were smaller as well. This renders them incompatible with any other variant. A final difference is found on the Enigma M4 where there is a fourth thin rotor. As the name suggests
it is slimmer than any other type of rotor. These rotors are not exchangeable with any other rotor or position in the mechanism.
Reflector
The reflector is a component which is similar to a rotor but on most cases it does not move. Its original name was Umkehrwalze (UKW). It completes the cryptographic process by
reflecting the signal back to the rotors extending the encryption cipher. Another characteristic is that it only has twenty-six contacts on the right side. It does not feature contacts on
the other side. This means that thirteen contacts are connected and reflected back through the remaining thirteen contacts. So when a character is entered through the leftmost rotor it is
reflected back into it. This gives a vital characteristic to the machine. As it is now self-reciprocated. Some models allow the reflector to be set to one of twenty-six positions but it
does not move during enciphering. Some machines also allowed the reflector to be replaced by another compatible one.
In 1944, UKW-D was released. It is based on the same principle as all other reflectors. The major difference came with the ability to rewire the reflector. This was an accessory that
proved to be very powerful by introducing further complexity. It did not have a great effect since it was introduced very late, almost at the end of the war.
The two known models that were compatible with the UKW-D were the Enigma KD and M4. It came as a standard with KD, where the original reflector and the left most rotor was replaced by
it. Enigma M4 is a similar story; in order to fit the UKW-D, the original thin reflector and thin rotor are removed and exchanged by it. In this sense M4 can now be regarded as a three
rotor machine.
Comparing the functionality of common reflectors to the UKW-D it is obvious that they have exactly the same functionality. The differences appear as the wiring can actually be altered
without the need of tools. The reflector has a cover that can be removed. Inside that there are twelve tightly packed cables that interconnect the twenty six contact points of the right
side of reflector.
Although there are twenty six contacts, only twenty four contacts are available to wire. This is due to the fact that there are space restrictions. Two contacts are missing and on
their place are retainers for holding the cover. The contacts that are missing are J and Y which are permanently interconnected. The contacts are arranged from A to Z in the ordinary
Enigma fashion with the two contacts described, simply missing. On this base, the reflector can be wired in many ways and therefore create a far more complex and unpredictable
machine.